It's VoIP hacker vs. VoIP Server. Who will lay the smack down and win this battle of good vs. evil? The stakes are high. If the hacker wins, it can mean thousands of dollars of phone charges, fraud, and potential liability, and a smug hacker who knows he got the best of your VoIP server.
A popular scam employed by VoIP criminals involves vhishing schemes. In Cisco's recent annual security report, they predicted VoIP as a potential area for cyber crime growth. According to IT World Canada, "The report mentions one recent vhishing scam targeting the U.S. Federal Deposit Insurance Corporation. Vhishers called U.S. consumers on mobile and land-line phones to inform them they were delinquent in loan payments that had been applied for over the Internet or made through a payday lender. Criminals were able to collect personal information, such as Social Security numbers from victims, according to the report."
SPIT (Spam over Internet Telephony) is becoming a problem, especially with hackers able to attack SIP servers that use simple SIP passwords to authenticate or they can brute-force attack to find passwords. Even worse they could initiate a distributed denial-of-service (DDOS) attack on the SIP server (thousands of attempted SIP registrations per second), bringing the phone system to its knees and crippling your business's voice communications.
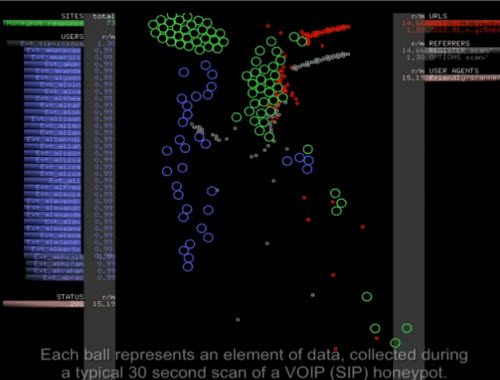
This brings me to this fascinating video I found. The video was created by Ben Reardon of Dataviz Australia who created a visualization of an attack on a VoIP server. In the video the VoIP server is on the left and the "good guy" SIP accounts of valid users that can make calls are shown as blue bubbles. The "bad guy" attack is shown on the right side of the video as white and red bubbles. These represent the scans from the hacker's computer program.
After first scanning for VoIP systems open to the outside/Internet (port 5060), the battle really commences with brute force attacking of extensions. The VoIP server then releases honeypots to enable security researchers collect the data from the honeyports to learn the tools, tactives, and motives of the attackers. The battle that plays out is slowed down to quarter speed. If the hacker's scans connect with the blue bubbles, it's game over and the hacker wins - full control of the VoIP server. To protect itself the VoIP server releases green honeypots to trap the hacker's scans. Then the hacker increases the number of scans to try and overwhelm the honeypots. As you can see in the video below, there can be only one winner (Is Charlie Sheen 'Winning'?). Place your bets now and play the video!
Tags: attack, ben reardon, dataviz, denial of service, hacker, hacking, honeypots, sip, spit, vhishing, voip Related tags: brute force, scans hacker, server releases, server, hacker, video
- Follow me:
 Facebook Profile
Facebook Profile FriendFeed Profile
FriendFeed Profile Google Reader Profile
Google Reader Profile LinkedIn Profile
LinkedIn Profile Netflix Profile
Netflix Profile Twitter Profile
Twitter Profile






Source: http://feedproxy.google.com/~r/voipgadgets/~3/iYTUV0p6_m4/voip-hacker-vs-voip-server-honeypots.asp
No comments:
Post a Comment